- Eliminate Attack Surfaces: Close Port 22 and remove the reliance on public-facing SSH or complex VPNs, significantly reducing your network's vulnerability.
- Identity-Aware Security: Implement granular access control based on verified user identity, ensuring only authorized personnel can interact with specific distributed endpoints.
- Identity-Aware Security: Implement granular access control including allowed folder and execution command definitions based on verified api key credentials, ensuring only authorized personnel can interact with specific distributed endpoints.
- Compliance-Ready Auditing: Maintain a comprehensive audit trail of all terminal interactions across your entire infrastructure for security reviews and compliance requirements.
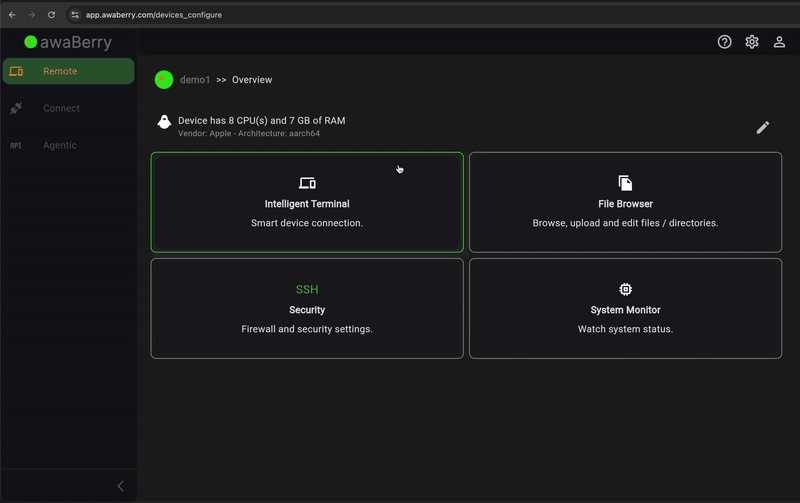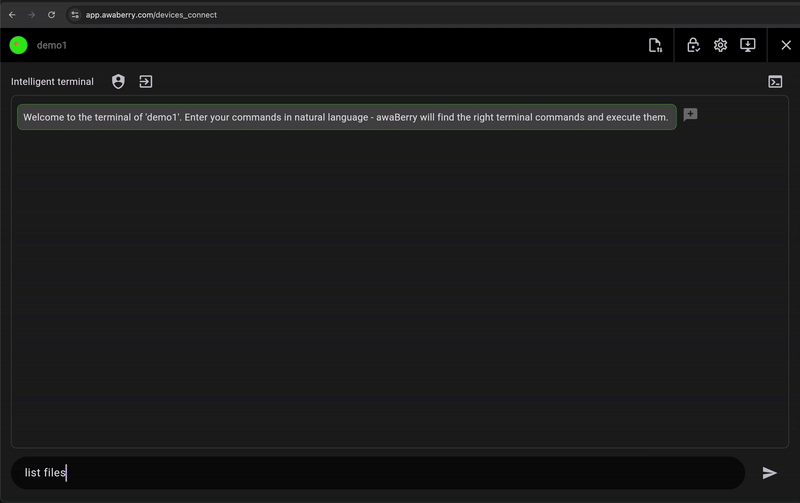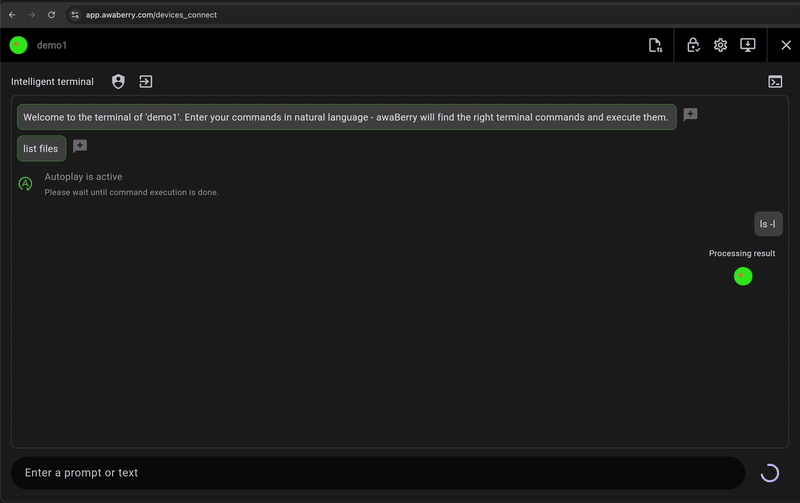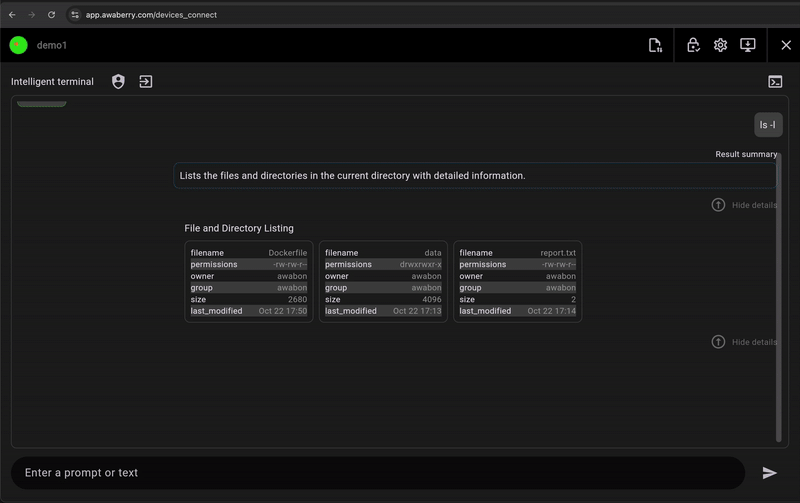
- Unified Fleet Management: Manage data center servers, cloud VMs, and embedded IoT devices through a single, secure, and encrypted command interface.
- Zero-Trust Connectivity: Every connection is protected by AES-256 end-to-end encryption, providing a secure bridge to any environment without compromising the perimeter.
- Boost Team Productivity: Provide developers, IT support, and engineers with instant access to the tools they need, from any browser, anywhere in the world.
- Accelerate Onboarding: Grant new team members or third-party contractors secure, time-bound access to specific devices in minutes, not hours.
- Smart & Efficient Workflows: The Agentic Command Interface and integrated file transfer reduce manual effort and errors, allowing your team to focus on high-value tasks.
- Universal Compatibility: One agent for Linux, macOS, Windows, and Docker ensures consistent security policies across your entire heterogeneous environment.
- Cloud-Agnostic by Design: Deploy seamlessly on AWS, Azure, Google Cloud, Hetzner, or your on-premise data center. Avoid vendor lock-in and maintain full control.
No need for VPN, reverse tunnel and open ports - a secure protocol by design with build in two-factor end to end encryption.
Learn more about the awaBerry Protocol →
Browser-Based Terminal
Zero-Trust Security
Agentic Command Interface
No SSH Required
Secure File Transfer
No VPN Required
Cloud Agnostic
Simple & Secure Setup
Linux Support
macOS Support
Windows Support
Docker Support
Zero-Trust Infrastructure Access is a security model that eliminates the need for traditional VPNs and open ports by requiring strict identity verification for every connection, regardless of where it originates. awaBerry implements this with end-to-end encryption and granular access controls.
awaBerry eliminates the need to expose Port 22 (SSH) to the internet. Instead, the awaBerry Client agent on your device establishes a secure outbound connection to awaBerry's infrastructure, allowing you to access your terminal through a web browser without any inbound firewall rules.
Identity-aware security means that access is granted based on verified user identity rather than network location. awaBerry implements granular access control, allowing you to define exactly which users can access which specific endpoints, with full audit trails.
Absolutely! awaBerry is cloud-agnostic and works seamlessly across AWS, Azure, Google Cloud, Hetzner, Digital Ocean, and on-premise data centers. You can manage your entire hybrid infrastructure from a single platform.
awaBerry Client supports Linux (all major distributions), macOS, Windows, and Docker containers. This universal compatibility ensures consistent security policies across your entire heterogeneous environment.
The Agentic Command Interface understands natural language commands, so you can describe what you want to do in plain language (e.g., 'show disk usage') and it will translate it into the correct shell commands. This reduces errors and accelerates diagnostics.
awaBerry provides comprehensive audit trails of all terminal interactions, implements strict access controls, and eliminates lateral movement risks by using outbound-only connections. This simplifies compliance auditing and demonstrates security best practices.
Yes! awaBerry Client can be integrated into your existing CI/CD pipelines and configuration management tools, enabling automated, large-scale deployments across your infrastructure.
Through awaBerry's web interface, you can grant secure, time-bound access to specific devices in minutes. Define exactly which endpoints each user can access and for how long, with full audit logging.
All connections are protected by AES-256 end-to-end encryption, ensuring that your data remains secure throughout the entire communication path.